Feb 11, 2016 | area, ccna, exam, Learn and Teach, OSPF, OSPF Questions 2, question, Quiz, test
CCNP ROUTE Practice Exam:
Multiarea OSPF 4
Chris Bryant, “The Computer Certification Bulldog”
Here’s the 4th practice exam in this series. Dig in!
Question 1:
You’re configuring an OSPF ASBR, and have determined that all the routes injected into OSPF via redistribution can be summarized with the address 23.0.0.0 /12.
What is the full OSPF command to advertise this summary into the OSPF domain in place of the specific routes?
Question 2:
You’re performing two-way route redistribution between an EIGRP AS and an OSPF domain. On the OSPF routers, what is the default routing table code for the routes learned from EIGRP?
Extra credit: What code will appear on the EIGRP routers next to any routes that are injected into the EIGRP AS from OSPF?
Consider the following OSPF configuration and answer the following questions.
R4(config)#router ospf 1
R4(config-router)#network 172.12.0.0 0.0.0.255 area 0
R4(config-router)#network 1.1.1.1 0.0.0.0 area 1
R4(config-router)#router-id 20.1.1.1
< router reloaded at this point >
R4(config)#interface loopback0
R4(config-if)#ip address 50.1.1.1 255.255.255.255
Question 3:
Is that a legal configuration? If not, why not?
Question 4:
What is the OSPF process number?
Question 5:
What is the RID of this particular router?
Question 6:
Is this router an ABR, ASBR, both, or neither?
Explain why this router is or isn’t an ABR.
Explain why this router is or isn’t an ASBR.
This ends the questions about that router configuration.
Question 7:
An OSPF total stub router can contain what route types?
A. Default route only
B. E2 routes and a default route
C. E1 routes and a default route
D. Intra-area routes and a default route
E. Inter-area routes and a default route
Answers:
1. The full command is:
summary-address 23.0.0.0 255.240.0.0
2. These routes will appear as OSPF External Type 2 routes and will have a router table code of “O E2”.
The routes that are redistributed from OSPF into EIGRP will appear in the EIGRP routing tables with a code of “D EX”.
3. Yep, it’s legal.
4. The OSPF process number is 1, as indicated by the router ospf 1 command.
5. The OSPF RID was hardcoded as 20.1.1.1, and it took effect after the router reload I mentioned.
6. This router is an ABR since it borders Area 1 and Area 0.
There is no route redistribution shown on this router, so it’s not an ASBR.
7. “D”. The routing table of a total stub router can contain intra-area routes and a default inter-area route using the ABR as the next hop.
Thanks for taking this CCNP practice exam – here are the other OSPF multiarea exams!
Feb 11, 2016 | ccna, exam, Learn and Teach, Networking, OSPF, OSPF Questions 2, questions, Quiz, test
Question 1
Into which two types of areas would an area border router (ABR) inject a default route? (Choose two)
A. the autonomous system of a different interior gateway protocol (IGP)
B. area 0
C. totally stubby
D. NSSA
E. stub
F. the autonomous system of an exterior gateway protocol (EGP)
Answer: C E
Explanation
Both stub area & totally stubby area allow an ABR to inject a default route. The main difference between these 2 types of areas is:
+ Stub area replaces LSA Type 5 (External LSA – created by an ASBR to advertise network from another autonomous system) with a default route
+ Totally stubby area replaces both LSA Type 5 and LSA Type 3 (Summary LSA – created by an ABR to advertise network from other areas, but still within the AS, sometimes called interarea routes) with a default route.
Below summarizes the LSA Types allowed and not allowed in area types:
| Area Type |
Type 1 & 2 (within area) |
Type 3 (from other areas) |
Type 4 |
Type 5 |
Type 7 |
| Standard & backbone |
Yes |
Yes |
Yes |
Yes |
No |
| Stub |
Yes |
Yes |
No |
No |
No |
| Totally stubby |
Yes |
No |
No |
No |
No |
| NSSA |
Yes |
Yes |
No |
No |
Yes |
| Totally stubby NSSA |
Yes |
No |
No |
No |
Yes |
Question 2
Which three restrictions apply to OSPF stub areas? (Choose three)
A. No virtual links are allowed.
B. The area cannot be a backbone area.
C. Redistribution is not allowed unless the packet is changed to a type 7 packet.
D. The area has no more than 10 routers.
E. No autonomous system border routers are allowed.
F. Interarea routes are suppressed.
Answer: A B E
Question 3
Refer to the partial configurations in the exhibit. What address is utilized for DR and BDR identification on Router1?
| Router1#show run**** output omitted ******
interface serial1/1
ipv6 address 2001:410:FFFE:1::64/64
ipv6 ospf 100 area 0
!
interface serial2/0
ipv6 address 3FFF:B00:FFFF:1::2/64
ipv6 ospf 100 area 0
!
ipv6 router ospf
router-id 10.1.1.3 |
A. the serial 1/1 address
B. the serial 2/0 address
C. a randomly generated internal address
D. the configured router-id address
Answer: D
Explanation
In OSPFv3 and OSPF version 2, the router uses the 32-bit IPv4 address to select the router ID for an OSPF process. The router ID selection process for OSPFv3 is described below (same as OSPF version 2):
1. The router ID is used if explicitly configured with the router-id command.
2. Otherwise, the highest IPv4 loopback address is used.
3. Otherwise, the highest active IPv4 address.
4. Otherwise, the router ID must be explicitly configured.
In this case the router ID 10.1.1.3 is explicitly configured -> D is correct.
Question 4
By default, which statement is correct regarding the redistribution of routes from other routing protocols into OSPF?
A. They will appear in the OSPF routing table as type E1 routes.
B. They will appear in the OSPF routing table as type E2 routes.
C. Summarized routes are not accepted.
D. All imported routes will be automatically summarized when possible.
E. Only routes with lower administrative distances will be imported.
Answer: B
Explanation
Type E1 external routes calculate the cost by adding the external cost to the internal cost of each link that the packet crosses while the external cost of E2 packet routes is always the external cost only. E2 is useful if you do not want internal routing to determine the path. E1 is useful when internal routing should be included in path selection. E2 is the default external metric when redistributing routes from other routing protocols into OSPF -> B is correct.
Question 5
Which statement is true about OSPF Network LSAs?
A. They are originated by every router in the OSPF network. They include all routers on the link, interfaces, the cost of the link, and any known neighbor on the link.
B. They are originated by the DR on every multi-access network. They include all attached routers including the DR itself.
C. They are originated by Area Border Routers and are sent into a single area to advertise destinations outside that area.
D. They are originated by Area Border Router and are sent into a single area to advertise an Autonomous System Border Router.
Answer: B
Explanation
Popular LSA Types are listed below:
| LSA Type |
Description |
Details |
| 1 |
Router LSA |
Generated by all routers in an area to describe their directly attached links |
| 2 |
Network LSA |
Advertised by the DR of the broadcast network (does not cross ABR) |
| 3 |
Summary LSA |
Advertised by the ABR of originating area |
| 4 |
Summary LSA |
Generated by the ABR of the originating area to advertise an ASBR to all other areas in the autonomous system |
| 5 |
AS external LSA |
Used by the ASBR to advertise networks from other autonomous systems |
| 7 |
Defined for NSSAs |
Generated by an ASBR inside a Not-so-stubby area (NSSA) to describe routes redistributed into the NSSA |
Question 6
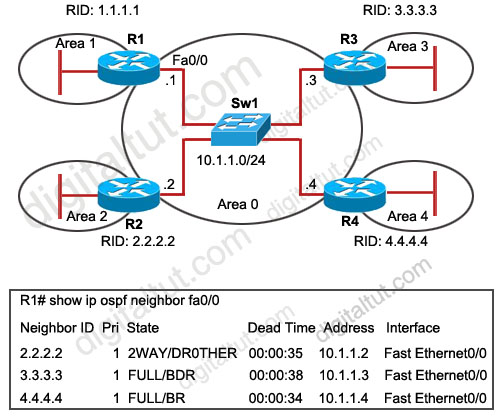
Refer to the exhibit. OSPF is configured on all routers in the network. On the basis of the show ip ospf neighbor output, what prevents R1 from establishing a full adjacency with R2?

A. Router R1 will only establish full adjacency with the DR and BDR on broadcast multiaccess networks.
B. Router R2 has been elected as a DR for the broadcast multiaccess network in OSPF area
C. Routers R1 and R2 are configured as stub routers for OSPF area 1 and OSPF area 2.
D. Router R1 and R2 are configured for a virtual link between OSPF area 1 and OSPF area 2.
E. The Hello parameters on routers R1 and R2 do not match.
Answer: A
Explanation
From the output, we learn that R4 is the DR and R3 is the BDR so other routers will only establish full adjacency with these routers. All other routers have the two-way adjacency established -> A is correct.
Question 7
Refer to the exhibit. On the basis of the configuration provided, how are the Hello packets sent by R2 handled by R5 in OSPF area 5?
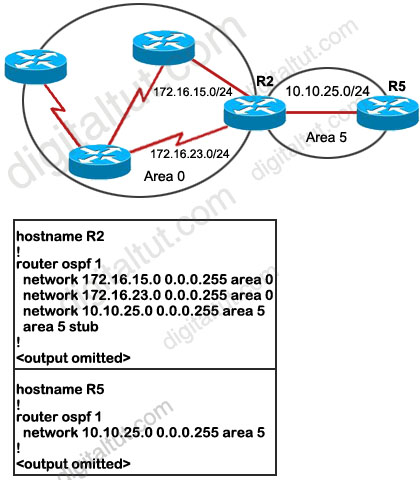
A. The Hello packets will be exchanged and adjacency will be established between routers R2 and R5.
B. The Hello packets will be exchanged but the routers R2 and R5 will become neighbors only.
C. The Hello packets will be dropped and no adjacency will be established between routers R2 and R5.
D. The Hello packets will be dropped but the routers R2 and R5 will become neighbors.
Answer: C
Explanation
Recall that in OSPF, two routers will become neighbors when they agree on the following: Area-id, Authentication, Hello and Dead Intervals, Stub area flag.
We must specify Area 5 as a stub area on the ABR (R2) and all the routers in that area (R5 in this case). But from the output, we learn that only R2 has been configured as a stub for Area 5. This will drop down the neighbor relationship between R2 and R5 because the stub flag is not matched in the Hello packets of these routers.
Question 8
When an OSPF design is planned, which implementation can help a router not have memory resource issues?
A. Have a backbone area (area 0) with 40 routers and use default routes to reach external destinations.
B. Have a backbone area (area 0) with 4 routers and 30,000 external routes injected into OSPF.
C. Have less OSPF areas to reduce the need for interarea route summarizations.
D. Have multiple OSPF processes on each OSPF router. Example, router ospf 1, router ospf 2
Answer: A
Question 9
When verifying the OSPF link state database, which type of LSAs should you expect to see within the different OSPF area types? (Choose three)
A. All OSPF routers in stubby areas can have type 3 LSAs in their database.
B. All OSPF routers in stubby areas can have type 7 LSAs in their database.
C. All OSPF routers in totally stubby areas can have type 3 LSAs in their database.
D. All OSPF routers in totally stubby areas can have type 7 LSAs in their database.
E. All OSPF routers in NSSA areas can have type 3 LSAs in their database.
F. All OSPF routers in NSSA areas can have type 7 LSAs in their database.
Answer: A E F
Explanation
Below summarizes the LSA Types allowed and not allowed in area types:
| Area Type |
Type 1 & 2 (within area) |
Type 3 (from other areas) |
Type 4 |
Type 5 |
Type 7 |
| Standard & backbone |
Yes |
Yes |
Yes |
Yes |
No |
| Stub |
Yes |
Yes |
No |
No |
No |
| Totally stubby |
Yes |
No |
No |
No |
No |
| NSSA |
Yes |
Yes |
No |
No |
Yes |
| Totally stubby NSSA |
Yes |
No |
No |
No |
Yes |
Popular LSA Types are listed below:
| LSA Type |
Description |
Details |
| 1 |
Router LSA |
Generated by all routers in an area to describe their directly attached links |
| 2 |
Network LSA |
Advertised by the DR of the broadcast network (does not cross ABR) |
| 3 |
Summary LSA |
Advertised by the ABR of originating area |
| 4 |
Summary LSA |
Generated by the ABR of the originating area to advertise an ASBR to all other areas in the autonomous system |
| 5 |
AS external LSA |
Used by the ASBR to advertise networks from other autonomous systems |
| 7 |
Defined for NSSAs |
Generated by an ASBR inside a Not-so-stubby area (NSSA) to describe routes redistributed into the NSSA |
Question 10
You are troubleshooting an OSPF problem where external routes are not showing up in the OSPF database. Which two options are valid checks that should be performed first to verify proper OSPF operation? (Choose two)
A. Are the ASBRs trying to redistribute the external routes into a totally stubby area?
B. Are the ABRs configured with stubby areas?
C. Is the subnets keyword being used with the redistribution command?
D. Is backbone area (area 0) contiguous?
E. Is the CPU utilization of the routers high?
Answer: A C
Explanation
A totally stubby stubby area cannot have an ASBR so it will discard this type of LSA (LSA Type 5) -> A is a valid check.
Each stubby area needs an ABR to communicate with other areas so it is normal -> B is not a valid check.
When pulling routes into OSPF, we need to use the keyword “subnets” so that subnets will be redistributed too. For example, if we redistribute these EIGRP routes into OSPF:
+ 10.0.0.0/8
+ 10.10.0.0/16
+ 10.10.1.0/24
without the keyword “subnets”
router ospf 1
redistribute eigrp 1
Then only 10.0.0.0/8 network will be redistributed because other routes are not classful routes, they are subnets. To redistribute subnets we must use the keyword “subnets”
router ospf 1
redistribute eigrp 1 subnets
-> C is a valid check.
We don’t need to care if area 0 is contiguous or not -> D is not a valid check.
CPU utilization cannot be the cause for this problem -> E is not a valid check.
For this question, please read our tutorial about OSPF LSA Types for more detail.

Feb 11, 2016 | ccna, hierarchical network, hierarchical network model, Learn and Teach, model, network
hierarchical network model
this source from: http://www.omnisecu.com/cisco-certified-network-associate-ccna/three-tier-hierarchical-network-model.php
Cisco suggests a Three−Tier (Three Layer) hierarchical network model, that consists of three layers: the Core layer, the Distribution layer, and the Access layer. Cisco Three-Layer network model is the preferred approach to network design.

The above picture can further explained based on below picture.
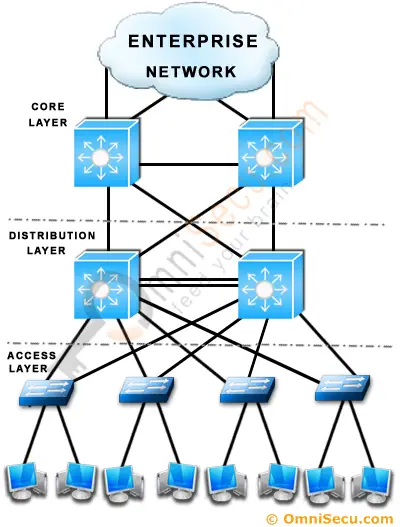
Core Layer
Core Layer consists of biggest, fastest, and most expensive routers with the highest model numbers and Core Layer is considered as the back bone of networks. Core Layer routers are used to merge geographically separated networks. The Core Layer routers move information on the network as fast as possible. The switches operating at core layer switches packets as fast as possible.
Distribution layer:
The Distribution Layer is located between the access and core layers. The purpose of this layer is to provide boundary definition by implementing access lists and other filters. Therefore the Distribution Layer defines policy for the network. Distribution Layer include high-end layer 3 switches. Distribution Layer ensures that packets are properly routed between subnets and VLANs in your enterprise.
Access layer
Access layer includes acces switches which are connected to the end devices (Computers, Printers, Servers etc). Access layer switches ensures that packets are delivered to the end devices.
Benefits of Cisco Three-Layer hierarchical model
The main benefits of Cisco Three-Layer hierarchical model is that it helps to design, deploy and maintain a scalable, trustworthy, cost effective hierarchical internetwork.
Better Performance: Cisco Three Layer Network Model allows in creating high performance networks
Better management & troubleshooting: Cisco Three Layer Network Model allows better network management and isolate causes of network trouble.
Better Filter/Policy creation and application: Cisco Three Layer Network Model allows better filter/policy creation application.
Better Scalability: Cisco Three Layer Network Model allows us to efficiently accomodate future growth.
Better Redundancy: Cisco Three Layer Network Model provides better redundancy. Multiple links across multiple devices provides better redundancy. If one switch is down, we have another alternate path to reach the destination.
another source : http://www.ciscopress.com/articles/article.asp?p=2202410&seqNum=4
Hierarchical Network Design Overview (1.1)
The Cisco hierarchical (three-layer) internetworking model is an industry wide adopted model for designing a reliable, scalable, and cost-efficient internetwork. In this section, you will learn about the access, distribution, and core layers and their role in the hierarchical network model.
Enterprise Network Campus Design (1.1.1)
An understanding of network scale and knowledge of good structured engineering principles is recommended when discussing network campus design.
Network Requirements (1.1.1.1)
When discussing network design, it is useful to categorize networks based on the number of devices serviced:
- Small network: Provides services for up to 200 devices.
- Medium-size network: Provides services for 200 to 1,000 devices.
- Large network: Provides services for 1,000+ devices.
Network designs vary depending on the size and requirements of the organizations. For example, the networking infrastructure needs of a small organization with fewer devices will be less complex than the infrastructure of a large organization with a significant number of devices and connections.
There are many variables to consider when designing a network. For instance, consider the example in Figure 1-1. The sample high-level topology diagram is for a large enterprise network that consists of a main campus site connecting small, medium, and large sites.
Network design is an expanding area and requires a great deal of knowledge and experience. The intent of this section is to introduce commonly accepted network design concepts.
NOTE
The Cisco Certified Design Associate (CCDA®) is an industry-recognized certification for network design engineers, technicians, and support engineers who demonstrate the skills required to design basic campus, data center, security, voice, and wireless networks.
Structured Engineering Principles (1.1.1.2)
Regardless of network size or requirements, a critical factor for the successful implementation of any network design is to follow good structured engineering principles. These principles include
- Hierarchy: A hierarchical network model is a useful high-level tool for designing a reliable network infrastructure. It breaks the complex problem of network design into smaller and more manageable areas.
- Modularity: By separating the various functions that exist on a network into modules, the network is easier to design. Cisco has identified several modules, including the enterprise campus, services block, data center, and Internet edge.
- Resiliency: The network must remain available for use under both normal and abnormal conditions. Normal conditions include normal or expected traffic flows and traffic patterns, as well as scheduled events such as maintenance windows. Abnormal conditions include hardware or software failures, extreme traffic loads, unusual traffic patterns, denial-of-service (DoS) events, whether intentional or unintentional, and other unplanned events.
- Flexibility: The ability to modify portions of the network, add new services, or increase capacity without going through a major forklift upgrade (i.e., replacing major hardware devices).
To meet these fundamental design goals, a network must be built on a hierarchical network architecture that allows for both flexibility and growth.
Hierarchical Network Design (1.1.2)
This topic discusses the three functional layers of the hierarchical network model: the access, distribution, and core layers.
Network Hierarchy (1.1.2.1)
Early networks were deployed in a flat topology as shown in Figure 1-2.
Hubs and switches were added as more devices needed to be connected. A flat network design provided little opportunity to control broadcasts or to filter undesirable traffic. As more devices and applications were added to a flat network, response times degraded, making the network unusable.
A better network design approach was needed. For this reason, organizations now use a hierarchical network design as shown in Figure 1-3.
A hierarchical network design involves dividing the network into discrete layers. Each layer, or tier, in the hierarchy provides specific functions that define its role within the overall network. This helps the network designer and architect to optimize and select the right network hardware, software, and features to perform specific roles for that network layer. Hierarchical models apply to both LAN and WAN design.
The benefit of dividing a flat network into smaller, more manageable blocks is that local traffic remains local. Only traffic that is destined for other networks is moved to a higher layer. For example, in Figure 1-3 the flat network has now been divided into three separate broadcast domains.
A typical enterprise hierarchical LAN campus network design includes the following three layers:
- Access layer: Provides workgroup/user access to the network
- Distribution layer: Provides policy-based connectivity and controls the boundary between the access and core layers
- Core layer: Provides fast transport between distribution switches within the enterprise campus
Another sample three-layer hierarchical network design is displayed in Figure 1-4. Notice that each building is using the same hierarchical network model that includes the access, distribution, and core layers.
 Figure 1-4 Multi Building Enterprise Network Design
Figure 1-4 Multi Building Enterprise Network Design
NOTE
There are no absolute rules for the way a campus network is physically built. While it is true that many campus networks are constructed using three physical tiers of switches, this is not a strict requirement. In a smaller campus, the network might have two tiers of switches in which the core and distribution elements are combined in one physical switch. This is referred to as a collapsed core design.
The Access Layer (1.1.2.2)
In a LAN environment, the access layer highlighted grants end devices access to the network. In the WAN environment, it may provide teleworkers or remote sites access to the corporate network across WAN connections.
As shown in Figure 1-5, the access layer for a small business network generally incorporates Layer 2 switches and access points providing connectivity between workstations and servers.
The access layer serves a number of functions, including
- Layer 2 switching
- High availability
- Port security
- QoS classification and marking and trust boundaries
- Address Resolution Protocol (ARP) inspection
- Virtual access control lists (VACLs)
- Spanning tree
- Power over Ethernet (PoE) and auxiliary VLANs for VoIP
The Distribution Layer (1.1.2.3)
The distribution layer aggregates the data received from the access layer switches before it is transmitted to the core layer for routing to its final destination. In Figure 1-6, the distribution layer is the boundary between the Layer 2 domains and the Layer 3 routed network.
The distribution layer device is the focal point in the wiring closets. Either a router or a multilayer switch is used to segment workgroups and isolate network problems in a campus environment.
A distribution layer switch may provide upstream services for many access layer switches.
The distribution layer can provide
- Aggregation of LAN or WAN links.
- Policy-based security in the form of access control lists (ACLs) and filtering.
- Routing services between LANs and VLANs and between routing domains (e.g., EIGRP to OSPF).
- Redundancy and load balancing.
- A boundary for route aggregation and summarization configured on interfaces toward the core layer.
- Broadcast domain control, because routers or multilayer switches do not forward broadcasts. The device acts as the demarcation point between broadcast domains.
The Core Layer (1.1.2.4)
The core layer is also referred to as the network backbone. The core layer consists of high-speed network devices such as the Cisco Catalyst 6500 or 6800. These are designed to switch packets as fast as possible and interconnect multiple campus components, such as distribution modules, service modules, the data center, and the WAN edge.
As shown in Figure 1-7, the core layer is critical for interconnectivity between distribution layer devices (for example, interconnecting the distribution block to the WAN and Internet edge).
The core should be highly available and redundant. The core aggregates the traffic from all the distribution layer devices, so it must be capable of forwarding large amounts of data quickly.
Considerations at the core layer include
- Providing high-speed switching (i.e., fast transport)
- Providing reliability and fault tolerance
- Scaling by using faster, and not more, equipment
- Avoiding CPU-intensive packet manipulation caused by security, inspection, quality of service (QoS) classification, or other processes
Two-Tier Collapsed Core Design (1.1.2.5)
The three-tier hierarchical design maximizes performance, network availability, and the ability to scale the network design.
However, many small enterprise networks do not grow significantly larger over time. Therefore, a two-tier hierarchical design where the core and distribution layers are collapsed into one layer is often more practical. A “collapsed core” is when the distribution layer and core layer functions are implemented by a single device. The primary motivation for the collapsed core design is reducing network cost, while maintaining most of the benefits of the three-tier hierarchical model.
The example in Figure 1-8 has collapsed the distribution layer and core layer functionality into multilayer switch devices.
The hierarchical network model provides a modular framework that allows flexibility in network design and facilitates ease of implementation and troubleshooting.
Activity 1.1.2.6: Identify Hierarchical Network Characteristics
Feb 11, 2016 | ccna, csico, exam, Learn and Teach, OSPF, Quiz, Routing Protocol, test
CCNP ROUTE Practice Exam Questions:
source: http://www.thebryantadvantage.com/CCNPExamBSCIPracticeExamMultiAreaOSPF3.htm
Multi-Area OSPF (Set #3)
Links to the other OSPF multiarea practice exams can be found at the end of the answers to this one.
As always with my practice exams, all multiple choice questions are “select all that apply”. Let’s get started!
Question 1:
The cost of an E2 route indicates what?
A. The cost of the path from the local router to the ASBR.
B. The cost of the path from the ASBR to the destination network.
C. The full cost of the path to the destination network from the local router.
D. The cost of the path from the ABR to the destination network.
Question 2:
What LSA type (numeric value) is generated by an ABR and describes inter-area links?
Question 3:
The cost of an E1 route indicates which of the following?
A. The cost of the path from the local router to the ASBR.
B. The cost of the path from the ASBR to the destination network.
C. The cost of the path from the local router to the destination network.
D. The cost of the path from the ASBR to the destination network.
Question 4:
By default, how does an OSPF routing table indicate routes that were injected into the OSPF domain via redistribution?
A. O EX
B. O *IA
C. O E2
D. O E1
E. O N2
Question 5:
Which of the following commands will show whether a router’s neighbors are or are not an ABR or ASBR?
A. show ip ospf database
B. show ip route ospf
C. show ip ospf neighbors
D. show ip ospf border-routers
Question 6:
You see a route marked “O IA” in your Cisco routing table. You know what the “O” stands for, or you wouldn’t be taking this exam. 🙂
However, what does the “IA” indicate regarding the destination network?
A. It’s in the same area as the local router.
B. It’s in another area.
C. It will be reached via a default route.
D. The route was learned via route redistribution.
Question 7:
What’s the number of the LSA type that is generated by every router for every area it belongs to, and is flooded to a single area?
Answers:
1. “B”. The default setting for a route learned by OSPF via redistribution is E2, and the metric of an E2 route is only the cost of the path from the ASBR to the destination network.
2. Type 3 LSAs are generated by ABRs and describe inter-area routes.
3. “C”. OSPF E1 routes reflect the entire cost of the path from the local router to the destination network.
4. “C”. As mentioned in the answer to Question 1. 🙂
5. “D”. It’s not one of the most common OSPF commands, but you can get some important information from the show ip ospf border-routers command.
6. “B”. The “IA” indicates a network that is in another OSPF area.
7. Type 1 LSAs are generated by every router for every area that it belongs to, and these LSAs are never flooded outside that particular area.
Thanks for taking this CCNP practice exam – here are the other OSPF multiarea exams on the site!
Feb 8, 2016 | ccna, EIGRP, EIGRP Questions 4, exam, Image, Learn and Teach, test
EIGRP Questions 4
Question 1
Which three statements are true about EIGRP route summarization? (Choose three)
A. Manual route summarization is configured in router configuration mode when the router is configured for EIGRP routing.
B. Manual route summarization is configured on the interface.
C. When manual summarization is configured, the summary route will use the metric of the largest specific metric of the summary routes.
D. The ip summary-address eigrp command generates a default route with an administrative distance of 90.
E. The ip summary-address eigrp command generates a default route with an administrative distance of 5.
F. When manual summarization is configured, the router immediately creates a route that points to null0 interface
Answer: B E F
[accordions handle=”arrows” space=”yes” icon_color=”#3c7206″ icon_current_color=”#ffffff”]
[accordion title=”Explaination” ][/accordion]
Explanation
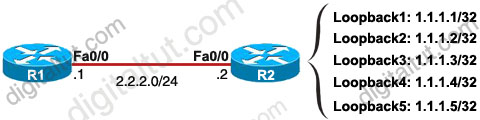
The ip summary-address eigrp {AS number} {address mask} command is used to configure a summary aggregate address for a specified interface. For example with the topology below:

R2 has 5 loopback interfaces but instead of advertising all these interfaces we can only advertise its summarized subnet. In this case the best summarized subnet should be 1.1.1.0/29 which includes all these 5 loopback interfaces.
R2(config)#interface fa0/0
R2(config-if)#ip summary-address eigrp 1 1.1.1.0 255.255.255.248
This configuration causes EIGRP to summarize network 1.1.1.0 and sends out Fa0/0 interface
After configuring manual EIGRP summary, the routing table of the local router will have a route to Null0:
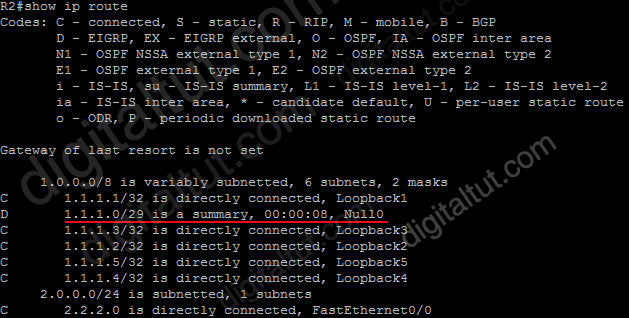
So why is this route inserted in the routing table when doing summarization? Well, you may notice that although our summarized subnet is 1.1.1.0/29 but we don’t have all IP addresses in this subnet. Assignable IP addresses of subnet 1.1.1.0/29 are from 1.1.1.1 to 1.1.1.6. Imagine what happens if R1 sends a packet to 1.1.1.6. Because R1 do believe R2 is connected with this IP so it will send this packet to R2. But R2 does not have this IP so if R2 has a default-route to R1 (for example R1 is connected to the Internet and R2 routes all unknown destination IP packets to R1) then a loop will occur.
To solve this problem, some routing protocols automatically add a route to Null0. A packet is sent to “Null0” means that packet is dropped. Suppose that R1 sends a packet to 1.1.1.6 through R2, even R2 does not have a specific route for that IP, it does have a general route pointing to Null0 which the packet sent to 1.1.1.6 can be matched -> That packet is dropped at R2 without causing a routing loop!
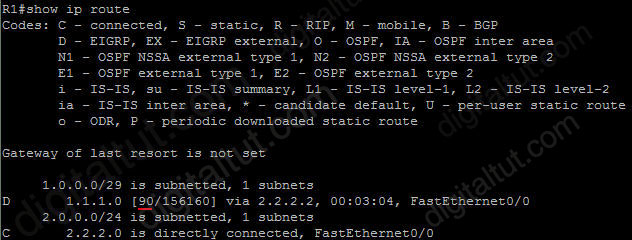
By default, EIGRP summary routes are given an administrative distance value of 5. Notice that this value is only shown on the local router doing the summarization. On other routers we can still see an administrative distance of 90 in their routing table.
[/accordions]
Question 2
After implementing EIGRP on your network, you issue the show ip eigrp traffic command on router C. The following output is shown:
RouterC#show ip eigrp traffic
IF-EIGRP Traffic Statistics for process 1
Hellos sent/received: 481/444
Updates sent/received: 41/32
Queries sent/received: 5/1
Replies sent/received: 1/4
Acks sent/received: 21/25
Input queue high water mark 2, 0 drops
SIA-Queries sent/received: 0/0
SIA-Replies sent/received: 0/0
Approximately 25 minutes later, you issue the same command again. The following output is shown:
RouterC#show ip eigrp traffic
IP-EIGRP Traffic Statistics for process 1
Hellos sent/received: 1057/1020
Updates sent/received: 41/32
Queries sent/received: 5/1
Replies sent/received: 1/4
Acks sent/received: 21/25
Input queue high water mark 2, 0 drops
SIA-Queries sent/received: 0/0
SIA-Replies sent/received: 0/0
Approximately 25 minutes later, you issue the same command a third time. The following output is shown:
RouterC#show ip eigrp traffic
IP-EIGRP Traffic Statistics for process 1
Hellos sent/received: 1754/1717
Updates sent/received: 41/32
Queries sent/received: 5/1
Replies sent/received: 1/4
Acks sent/received: 21/25
Input queue high water mark 2, 0 drops
SIA-Queries sent/received: 0/0
SIA-Replies sent/received: 0/0
What can you conclude about this network?
A. The network has been stable for at least the last 45 minutes.
B. There is a flapping link or interface, and router C knows an alternate path to the network.
C. There is a flapping link or interface, and router A does not know an alternate path to the network.
D. EIGRP is not working correctly on router C.
E. There is not enough information to make a determination.
Answer: A
[accordions handle=”arrows” space=”yes” icon_color=”#3c7206″ icon_current_color=”#ffffff”]
[accordion title=”Explaination” ]
Explanation
In three times using the command, the “Queries sent/received” & “Replies sent/received” are still the same -> the network is stable.
[/accordion]
[/accordions]
Question 3
After implementing EIGRP on your network, you issue the show ip eigrp traffic command on router C. The following output is shown:
RouterC#show ip eigrp traffic
IP-EIGRP Traffic Statistics for process 1
Hellos sent/received: 2112/2076
Updates sent/received: 47/38
Queries sent/received: 5/3
Replies sent/received: 3/4
Acks sent/received: 29/33
Input queue high water mark 2, 0 drops
SIA-Queries sent/received: 0/0
SIA-Replies sent/received: 0/0
Moments later, you issue the same command a second time and the following output is shown:
RouterC#show ip eigrp traffic
IP-EIGRP Traffic Statistics for process 1
Hellos sent/received: 2139/2104
Updates sent/received: 50/39
Queries sent/received: 5/4
Replies sent/received: 4/4
Acks sent/received: 31/37
Input queue high water mark 2, 0 drops
SIA-Queries sent/received: 0/0
SIA-Replies sent/received: 0/0
Moments later, you issue the same command a third time and the following output is shown:
RouterC#show ip eigrp traffic
IP-EIGRP Traffic Statistics for process 1
Hellos sent/received: 2162/2126
Updates sent/received: 53/42
Queries sent/received: 5/5
Replies sent/received: 5/4
Acks sent/received: 35/41
Input queue high water mark 2, 0 drops
SIA-Queries sent/received: 0/0
SIA-Replies sent/received: 0/0
What information can you determine about this network?
A. The network is stable.
B. There is a flapping link or interface, and router C knows an alternate path to the network.
C. There is a flapping link or interface, and router C does not know an alternate path to the network.
D. EIGRP is not working correctly on router C.
E. There is not enough information to make a determination.
Answer: B
[accordions handle=”arrows” space=”yes” icon_color=”#3c7206″ icon_current_color=”#ffffff”]
[accordion title=”Explaination” ]
Explanation
We notice that the “Queries received” number is increased so router C has been asked for a route. The “Replies sent” number is also increased -> router C knows an alternate path to the network.
[/accordion]
[/accordions]
Question 4
R1 and R2 are connected and are running EIGRP on all their interfaces, R1 has four interfaces, with IP address 172.16.1.1/24, 172.16.2.3/24,172.16.5.1/24, and 10.1.1.1/24. R2 has two interfaces, with IP address 172.16.1.2/24 and 192.168.1.1/24. There are other routers in the network that are connected on each of the interfaces of these two routers that are also running EIGRP. Which summary routes does R1 generate automatically (assuming auto-summarization is enable)? (choose two)
A. 192.168.1.0/24
B. 10.0.0.0/8
C. 172.16.1.0/22
D. 172.16.0.0/16
E. 10.1.1.0/24
Answer: B D
Question 5
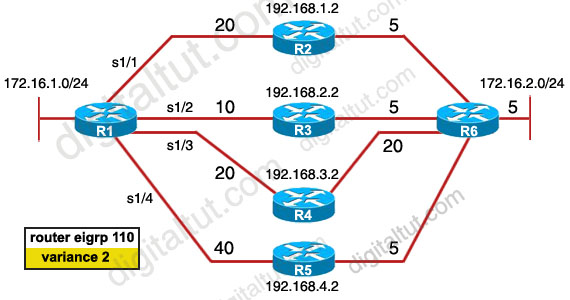
There was an exhibit, 172.16.1.0/24 to 172.16.2.0/24 with the 4 paths with mentions of eigrp metric and asked if the variance is put to 2 in exhibit then what 2 paths are not used by eigrp routing table? (Choose two)
A. R1—R2—R6
B. R1—R3—R6
C. R1—R4—R6
D. R1—R5—R6
Answer: C D
Question 6
What does the default value of the EIGRP variance command of 1 mean?
A. Load balancing is disabled on this router.
B. The router performs equal-cost load balancing.
C. Only the path that is the feasible successor should be used.
D. The router only performs equal-cost load balancing on all paths that have a metric greater than 1.
Answer: B
Question 7
Refer to the exhibit. EIGRP has been configured on all routers in the network. The command metric weights 0 0 1 0 0 has been added to the EIGRP process so that only the delay metric is used in the path calculations. Which router will R1 select as the successor and feasible successor for Network A?
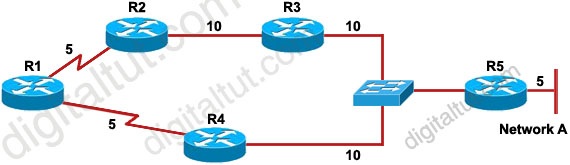
A. R4 becomes the successor for Network A and will be placed in the routing table. R2 becomes the feasible successor for Network A.
B. R4 becomes the successor for Network A and will be included in the routing table. No feasible successor will be selected as the advertised distance from R2 is higher than the feasible distance.
C. R2 becomes the successor and will be placed in the routing table. R4 becomes the feasible successor for Network A.
D. R2 becomes the successor and will be placed in the routing table. No feasible successor will be selected as the reported distance from R4 is lower than the feasible distance.
Answer: B
Question 8
Based on the exhibited output, which three statements are true? (Choose three)
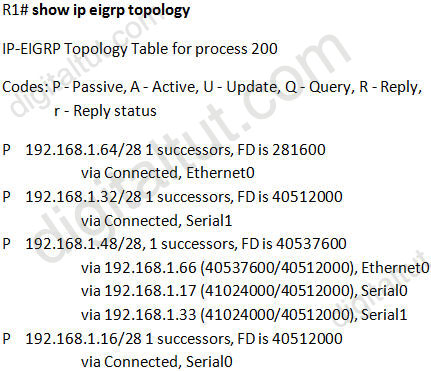
A. R1 is in AS 200.
B. R1 will load balance between three paths to reach the 192.168.1.48/28 prefix because all three paths have the same advertised distance (AD) of 40512000.
C. The best path for R1 to reach the 192.168.1.48/28 prefix is via 192.168.1.66.
D. 40512000 is the advertised distance (AD) via 192.168.1.66 to reach the 192.168.1.48/28 prefix.
E. All the routes are in the passive mode because these routes are in the hold-down state.
F. All the routes are in the passive mode because R1 is in the query process for those routes.
Answer: A C D
[accordions handle=”arrows” space=”yes” icon_color=”#3c7206″ icon_current_color=”#ffffff”]
[accordion title=”Explaination” ]
Explanation
In the statement “IP-EIGRP Topology Table for process 200”, process 200 here means AS 200 -> A is correct.
There are 3 paths to reach network 192.168.1.48/28 but there is only 1 path in the routing table (because there is only 1 successor) so the path with least FD will be chosen -> path via 192.168.1.66 with a FD of 40537600 will be chosen -> C is correct.
The other parameter, 40512000, is the AD of that route -> D is correct.
[/accordion]
[/accordions]
Question 9
Characteristics of the routing protocol EIGRP? (choose two)
A. Updates are sent as broadcast.
B. Updates are sent as multicast.
C. LSAs are sent to adjacent neighbors.
D. Metric values are represented in a 32-bit format for granularity.
Answer: B D
[accordions handle=”arrows” space=”yes” icon_color=”#3c7206″ icon_current_color=”#ffffff”]
[accordion title=”Explaination” ]
Explanation
EIGRP updates are sent as multicast to address 224.0.0.10 -> B is correct.
EIGRP metric values, for example an entry in the “show ip route” command:
D 10.1.21.128/27 [90/156160] via 10.1.4.5, 00:00:21, FastEthernet1/0/1
EIGRP metric here is 156160 and it is a 32-bit value. For more information please read here:
http://www.cisco.com/c/en/us/products/collateral/ios-nx-os-software/enhanced-interior-gateway-routing-protocol-eigrp/whitepaper_C11-720525.html
[/accordion]
[/accordions]
Question 10
Which EIGRP packet statement is true?
A. On high-speed links, hello packets are broadcast every 5 seconds for neighbor discovery.
B. On low-speed links, hello packets are broadcast every 15 seconds for neighbor discovery.
C. Reply packets are multicast to IP address 224.0.0.10 using RTP.
D. Update packets route reliable change information only to the affected routers.
E. Reply packets are used to send routing updates.
Answer: D
Feb 8, 2016 | ccna, EIGRP, EIGRP Questions 3, exam, Image, Learn and Teach, Quiz, test
Here you will find answers to EIGRP Questions – Part 3
Note: If you are not sure about EIGRP, please read my EIGRP tutorial.
Question 1
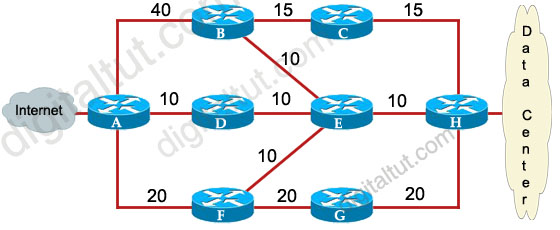
Refer to the exhibit. ROUTE.com has just implemented this EIGRP network. A network administrator came to you for advice while trying to implement load balancing across part of their EIGRP network.
If the variance value is configured as 2 on all routers and all other metric and K values are configured to their default values, traffic from the Internet to the data center will be load balanced across how many paths?

A. 1
B. 2
C. 3
D. 4
Answer: C
Explanation
First we should list all the paths from the Internet to the data center:
+ A-B-C-H with a metric of 70 (40 + 15 + 15)
+ A-B-E-H with a metric of 60 (40+10+10)
+ A-D-E-H with a metric of 30 (10+10+10)
+ A-D-E-B-C-H with a metric of 60 (10+10+10+15+15)
+ A-D-E-F-G-H with a metric of 70 (10+10+10+20+20)
+ A-F-G-H with a metric of 60 (20+20+20)
+ A-F-E-H with a metric of 40 (20+10+10)
So the path A-D-E-H will be chosen because it has the best metric. But EIGRP can support unequal cost path load balancing. By configuring the variance value of 2, the minimum metric is increased to 60 (30 * 2) and all the routes that have a metric of less than or equal to 60 and satisfy the feasibility condition will be used to send traffic.
Besides the main path A-D-E-H we have 4 more paths that have the metric of less than or equal to 60 (we also include the Advertised Distances of these routes for later comparison):
+ A-B-E-H with an AD of 20
+ A-D-E-B-C-H with an AD of 50
+ A-F-G-H with an AD of 40
+ A-F-E-H with an AD of 20
Now the last thing we need to consider is the feasible condition. The feasible condition states:
“To qualify as a feasible successor, a router must have an AD less than the FD of the current successor route”
The FD of the current successor route here is 30 (notice that the variance number is not calculated here). Therefore there are only 2 paths that can satisfy this conditions: the path A-B-E-H & A-F-E-H.
In conclusion, traffic from the Internet to the data center will be load balanced across 3 paths, including the main path (successor path) -> C is correct.
Question 2
Which condition must be satisfied before an EIGRP neighbor can be considered a feasible successor?
A. The neighbor’s advertised distance must be less than or equal to the feasible distance of the current successor.
B. The neighbor’s advertised distance must be less than the feasible distance of the current successor.
C. The neighbor’s advertised distance must be greater than the feasible distance of the current successor.
D. The neighbor’s advertised distance must be equal to the feasible distance of the current successor.
E. The neighbor’s advertised distance must be greater than or equal to the feasible distance of the current successor.
Answer: B
Explanation
As explained in question 1, this is called the feasible condition.
Question 3
Which statement about a non-zero value for the load metric (k2) for EIGRP is true?
A. A change in the load on an interface will cause EIGRP to recalculate the routing metrics and send a corresponding update out to each of its neighbors.
B. EIGRP calculates interface load as a 5-minute exponentially weighted average that is updated every 5 minutes.
C. EIGRP considers the load of an interface only when sending an update for some other reason.
D. A change in the load on an interface will cause EIGRP to recalculate and update the administrative distance for all routes learned on that interface.
Answer: C
Explanation
The load metric (k2) represents the worst load on a link between source and destination.
EIGRP routing updates are triggered only by a change in network topology (like links, interfaces go up/down, router added/removed), and not by change in interface load or reliability -> A & D are not correct.
The load is a five minute exponentially weighted average that is updated every five seconds (not five minutes) -> B is not correct.
EIGRP considers the load of an interface only when sending an update for some other reason (like a link failure, topology change). Updates are not sent out each time the load changes -> C is correct.
Note: To learn how to calculate EIGRP metric, please read my EIGRP tutorial – Part 3.
Question 4
Your network consists of a large hub-and-spoke Frame Relay network with a CIR of 56 kb/s for each spoke.
Which statement about the selection of a dynamic protocol is true?
A. EIGRP would be appropriate if LMI type ANSI is NOT used.
B. EIGRP would be appropriate, because the Frame Relay spokes could be segmented into their own areas.
C. EIGRP would be appropriate, because by default, queries are not propagated across the slow speed Frame Relay links.
D. EIGRP would be appropriate, because you can manage how much bandwidth is consumed over the Frame Relay interface.
Answer: D
Explanation
By default, EIGRP will limit itself to using no more than 50% of the interface bandwidth. The primary benefit of controlling EIGRP’s bandwidth usage is to avoid losing EIGRP packets, which could occur when EIGRP generates data faster than the interface line can absorb it. This is of particular benefit on Frame Relay networks, where the access interface bandwidth and the PVC capacity may be very different.
For example, in our Frame Relay topology a Hub is connected with 4 Spoke routers. The main Frame Relay interface on Hub router is 512Kpbs which is not enough to use for 6 links of 128 Kbps ( = 768 Kbps).
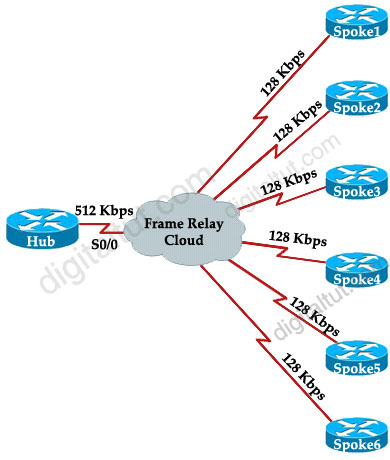
The solution here is we can use 512 / 6 = 85 Kbps on each subinterface of Hub by using “bandwidth 85” command. For example:
Hub(config)#interface Serial0/0.1 point-to-point
Hub(config-subif)#bandwidth 85
Also on Spoke routers we need to set this value. For example on Spoke1:
Spoke1(config)#interface Serial0/1.0 point-to-point
Spoke1(config-subif)#bandwidth 85
Notice that by default, EIGRP limits itself to use no more than 50% of the configured interface bandwidth. In this case EIGRP will not use more than 42.5 Kbps (50% of 85 Kbps).
(For more information about implementing EIGRP over Frame Relay, please read http://www.cisco.com/en/US/tech/tk365/technologies_tech_note09186a0080094063.shtml)
Question 5
When an EIGRP topology change is detected, what is the correct order of events when there is a FS?
A.
The neighbor adjacency is deleted.
The feasible route is used.
DUAL is notified.
Remove all topology entries learned from that neighbor.
B.
DUAL is notified.
Remove all topology entries learned from that neighbor.
The neighbor adjacency is deleted.
Routes enter the Active state and the feasible route is used.
C.
The neighbor adjacency is deleted.
Routes enter the Active state and the feasible route is used.
DUAL is notified.
Remove all topology entries learned from that neighbor.
D.
DUAL is notified.
The neighbor adjacency is deleted.
Remove all topology entries learned from that neighbor.
The feasible route is used.
Answer: D
Question 6
Refer to the exhibit. You want to use all the routes in the EIGRP topology for IP load balancing.
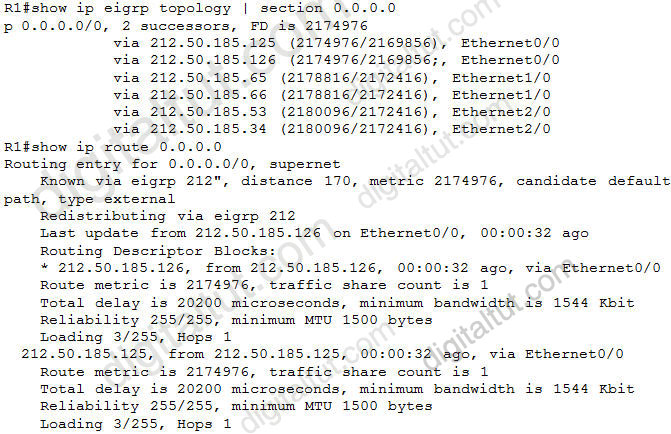
Which two EIGRP subcommands would you use to accomplish this goal? (Choose two)
A. traffic-share balanced
B. distance
C. maximum-paths
D. default-network
E. variance
Answer: C E
Explanation
Notice that the “maximum-paths” command is used to share traffic to equal cost path while the “variance” command can share traffic to unequal cost path.
In the output above we learn that EIGRP is using 2 successors to send traffic. By using the “variance 2” command we can share traffic to other feasible successor routes. But by default, EIGRP only shares traffic to 4 paths. So we need to use the “maximum-paths 6” to make sure all of these routes are used.
Question 7
Refer to the exhibit. R1 accesses the Internet using E0/0. You have been asked to configure R1 so that a default route is generated to its downstream devices (191.0.0.1 and 192.0.0.1). Which commands would create this configuration?
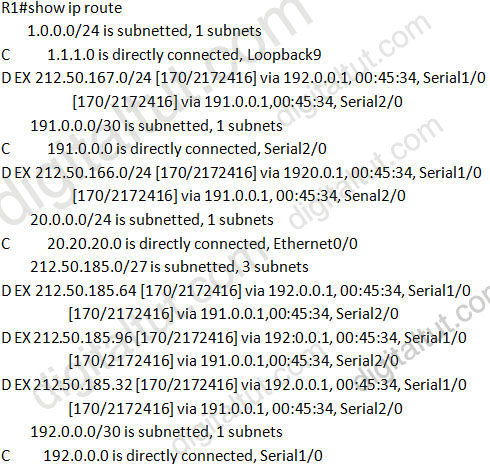
A.
router eigrp 190
redistribute static
!
ip route 0.0.0.0 0.0.0.0 Null0
B. ip default-network 20.0.0.0
C.
router eigrp 190
redistribute static
!
ip route 0.0.0.0 255.255.255.255 Null0
D. ip default-network 20.20.20.0
Answer: A
Question 8
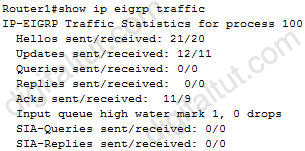
Which command will display EIGRP packets sent and received, as well as statistics on hello packets, updates, queries, replies, and acknowledgments?
A. debug eigrp packets
B. show ip eigrp traffic
C. debug ip eigrp
D. show ip eigrp interfaces
Answer: B
Explanation
Below is the output of the “show ip eigrp traffic” command:
Question 9
Which three statements are true about EIGRP operation? (Choose three)
A. When summarization is configured, the router will also create a route to null 0.
B. The summary route remains in the route table, even if there are no more specific routes to the network.
C. Summarization is configured on a per-interface level.
D. The maximum metric for the specific routes is used as the metric for the summary route.
E. Automatic summarization across major network boundaries is enabled by default.
Answer: A C E
Question 10
Which two statements about the EIGRP DUAL process are correct? (Choose two)
A. An EIGRP route will go active if there are no successors or feasible successors in the EIGRP topology table.
B. An EIGRP route will go passive if there are no successors in the EIGRP topology table.
C. DUAL will trigger an EIGRP query process while placing the flapping routes in the holddown state.
D. A feasible successor in the EIGRP topology table can become the successor only after all the query requests have been replied to.
E. The stuck in active state is caused when the wait for the query replies have timed out.
F. EIGRP queries are sent during the loading state in the EIGRP neighbor establishment process.
Answer: A E
Question 11
What are three key concepts that apply when configuring the EIGRP stub routing feature in a hub and spoke network? (Choose three)
A. A hub router prevents routes from being advertised to the remote router.
B. Only remote routers are configured as stubs.
C. Stub routers are not queried for routes.
D. Spoke routers connected to hub routers answer the route queries for the stub router.
E. A stub router should have only EIGRP hub routers as neighbors.
F. EIGRP stub routing should be used on hub routers only.
Answer: B C E



























